- Topic1/3
10k Popularity
29k Popularity
13k Popularity
6k Popularity
172k Popularity
- Pin
- Hey fam—did you join yesterday’s [Show Your Alpha Points] event? Still not sure how to post your screenshot? No worries, here’s a super easy guide to help you win your share of the $200 mystery box prize!
📸 posting guide:
1️⃣ Open app and tap your [Avatar] on the homepage
2️⃣ Go to [Alpha Points] in the sidebar
3️⃣ You’ll see your latest points and airdrop status on this page!
👇 Step-by-step images attached—save it for later so you can post anytime!
🎁 Post your screenshot now with #ShowMyAlphaPoints# for a chance to win a share of $200 in prizes!
⚡ Airdrop reminder: Gate Alpha ES airdrop is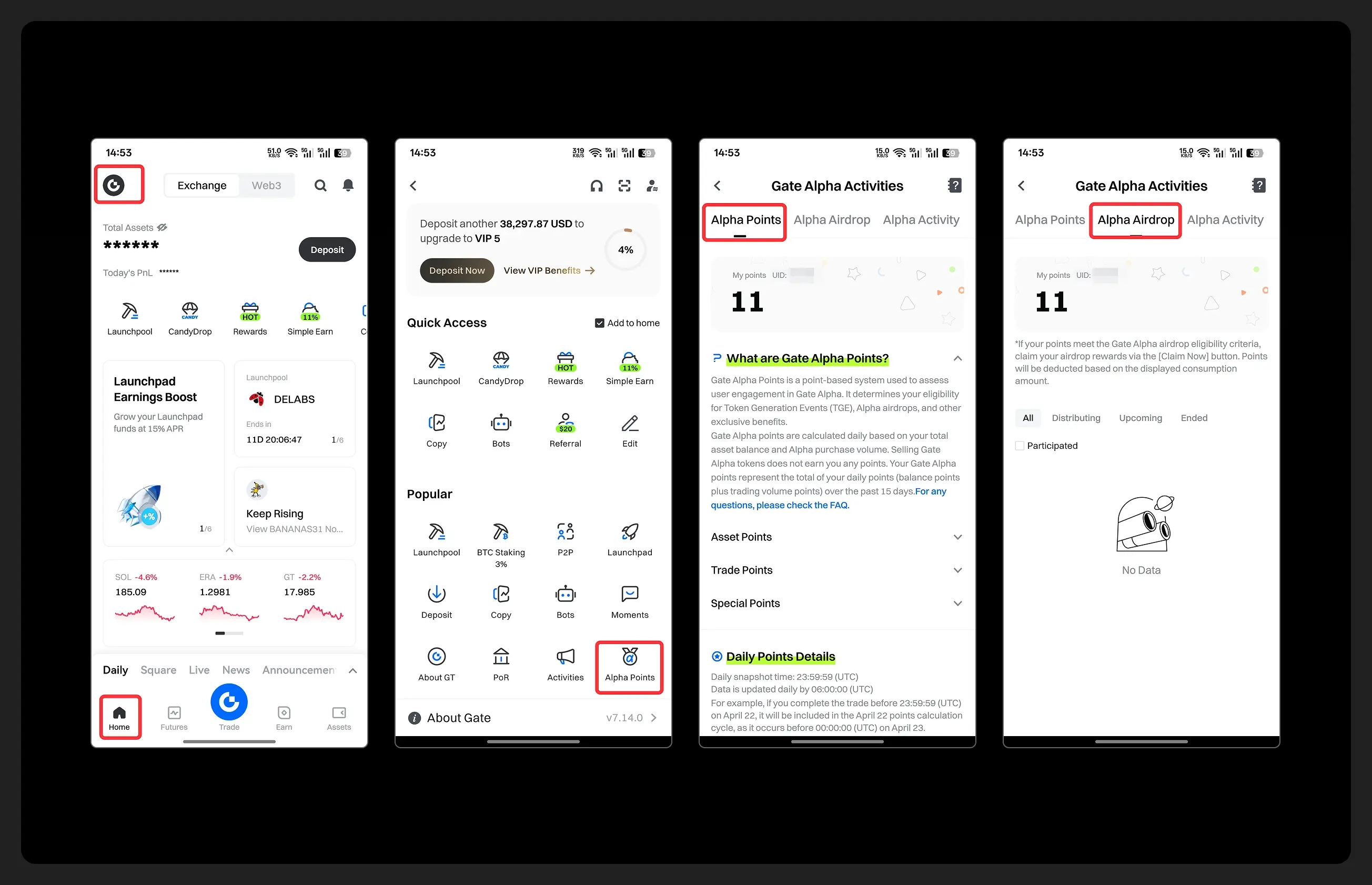
- Gate Futures Trading Incentive Program is Live! Zero Barries to Share 50,000 ERA
Start trading and earn rewards — the more you trade, the more you earn!
New users enjoy a 20% bonus!
Join now:https://www.gate.com/campaigns/1692?pid=X&ch=NGhnNGTf
Event details: https://www.gate.com/announcements/article/46429
- Hey Square fam! How many Alpha points have you racked up lately?
Did you get your airdrop? We’ve also got extra perks for you on Gate Square!
🎁 Show off your Alpha points gains, and you’ll get a shot at a $200U Mystery Box reward!
🥇 1 user with the highest points screenshot → $100U Mystery Box
✨ Top 5 sharers with quality posts → $20U Mystery Box each
📍【How to Join】
1️⃣ Make a post with the hashtag #ShowMyAlphaPoints#
2️⃣ Share a screenshot of your Alpha points, plus a one-liner: “I earned ____ with Gate Alpha. So worth it!”
👉 Bonus: Share your tips for earning points, redemption experienc
- 🎉 The #CandyDrop Futures Challenge is live — join now to share a 6 BTC prize pool!
📢 Post your futures trading experience on Gate Square with the event hashtag — $25 × 20 rewards are waiting!
🎁 $500 in futures trial vouchers up for grabs — 20 standout posts will win!
📅 Event Period: August 1, 2025, 15:00 – August 15, 2025, 19:00 (UTC+8)
👉 Event Link: https://www.gate.com/candy-drop/detail/BTC-98
Dare to trade. Dare to win.
The Resilience of the SUI Ecosystem: Technical Reflections and Long-term Rise Potential After the Cetus Incident
Firm Belief After the Security Crisis: Why SUI Still Has Long-term Rise Potential?
TL;DR
The essence of this attack lies in the lack of boundary checks in the arithmetic functions of the Cetus protocol------a logical vulnerability caused by overly broad masking and bit shift overflow, which is unrelated to the resource security model of the SUI chain or the Move language. The vulnerability can be fixed with "a line of boundary check" and does not affect the core security of the entire ecosystem.
Although SUI adopts a slightly centralized tendency with features such as DPoS validator rounds and blacklist freezing, this has proven useful in the CETUS incident response: validators quickly synchronized malicious addresses to the Deny List and refused to package related transactions, resulting in the instant freezing of over $160 million in funds. This is essentially a form of proactive "on-chain Keynesianism," where effective macro control plays a positive role in the economic system.
Mathematics and boundary verification: Introduce upper and lower limit assertions for all critical arithmetic operations (such as shifts, multiplications, and divisions), and conduct extreme value fuzzing and formal verification. Additionally, there is a need to enhance auditing and monitoring: beyond general code audits, add a specialized mathematical audit team and real-time on-chain transaction behavior detection to catch abnormal splits or large flash loans early.
In the Cetus incident, SUI effectively collaborated with the project team to successfully freeze over 160 million USD in funds and promote a 100% compensation plan, demonstrating strong on-chain responsiveness and ecological responsibility. The SUI Foundation also added 10 million USD in audit funds to strengthen the security defenses. In the future, mechanisms such as on-chain tracking systems, community-built security tools, and decentralized insurance can be further promoted to improve the funding guarantee system.
SUI has rapidly achieved a transition from "new chain" to "strong ecosystem" in less than two years, building a diversified ecological landscape covering multiple tracks such as stablecoins, DEX, infrastructure, DePIN, and gaming. The total scale of stablecoins has exceeded $1 billion, providing a solid liquidity foundation for DeFi modules; TVL ranks 8th globally, trading activity ranks 5th globally, and 3rd among non-EVM networks (only behind Bitcoin and Solana), demonstrating strong user participation and asset accumulation capabilities.
1. A chain reaction triggered by an attack.
On May 22, 2025, the leading AMM protocol Cetus deployed on the SUI network suffered a hacker attack. The attacker exploited a logical vulnerability related to the "integer overflow issue" to initiate precise manipulation, resulting in the loss of over $200 million in assets. This incident is not only one of the largest security incidents in the DeFi space so far this year but also the most destructive hacker attack since the launch of the SUI mainnet.
According to DefiLlama data, the total TVL of the SUI blockchain plummeted by over $330 million on the day of the attack, and the amount locked in the Cetus protocol evaporated by 84%, dropping to $38 million. As a result, several popular tokens on SUI (including Lofi, Sudeng, Squirtle, etc.) fell by 76% to 97% within just one hour, raising widespread concerns in the market about the security and ecological stability of SUI.
However, after this shockwave, the SUI ecosystem has demonstrated strong resilience and recovery capability. Although the Cetus incident caused fluctuations in confidence in the short term, on-chain funds and user activity did not experience a sustained decline; instead, it significantly prompted the entire ecosystem to enhance its focus on security, infrastructure development, and project quality.
Klein Labs will analyze the reasons behind this attack event, the node consensus mechanism of SUI, the security of the MOVE language, and the ecological development of SUI, to outline the current ecological landscape of this public chain that is still in its early development stage, and discuss its future development potential.
2. Analysis of the Causes of the Cetus Incident Attack
2.1 Attack Implementation Process
According to the technical analysis of the Cetus attack incident by the Slow Fog team, the hacker successfully exploited a critical arithmetic overflow vulnerability in the protocol, utilizing flash loans, precise price manipulation, and contract flaws to steal over $200 million in digital assets in a short period. The attack path can be roughly divided into the following three stages:
①Initiate flash loan, manipulate price
The hackers first leveraged a maximum slippage flash exchange of 10 billion haSUI flash loans, borrowing a large amount of funds to manipulate prices.
Flash loans allow users to borrow and repay funds in a single transaction, only requiring a fee, characterized by high leverage, low risk, and low cost. Hackers exploited this mechanism to drive down market prices within a short period and precisely controlled it within a very narrow range.
The attacker then prepares to create an extremely narrow liquidity position, precisely setting the price range between the lowest quote of 300,000 and the highest price of 300,200, with a price width of only 1.00496621%.
By the above methods, the hacker successfully manipulated the haSUI price using a sufficient number of tokens and huge liquidity. Subsequently, they also targeted several tokens with no real value for manipulation.
②Add liquidity
The attacker creates a narrow liquidity position, claiming to add liquidity, but due to a vulnerability in the checked_shlw function, ultimately only receives 1 token.
Essentially due to two reasons:
Mask settings are too wide: equivalent to a very large liquidity addition limit, resulting in the contract's validation of user inputs being ineffective. Hackers bypassed overflow detection by setting abnormal parameters, constructing inputs that are always less than this limit.
Data overflow was truncated: When performing the shift operation n << 64 on the numeric value n, data truncation occurred because the shift exceeded the effective bit width of the uint256 data type (256 bits). The overflow portion of the high bits was automatically discarded, resulting in a calculation far below expectations, causing the system to underestimate the amount of haSUI required for the exchange. The final computed result was about less than 1, but since it was rounded up, the final result equaled 1, meaning the hacker only needed to add 1 token to exchange for substantial liquidity.
③Withdraw liquidity
Repay the flash loan and retain substantial profits. Ultimately withdraw token assets worth hundreds of millions of dollars from multiple liquidity pools.
The situation of fund loss is serious, and the attack resulted in the following assets being stolen:
12.9 million SUI (approximately 54 million USD)
60 million USDC
4.9 million USD Haedal Staked SUI
19.5 million USD TOILET
Other tokens such as HIPPO and LOFI have dropped by 75--80%, liquidity has dried up.
2.2 Causes and Characteristics of This Vulnerability
The vulnerability of Cetus has three characteristics:
The cost of fixing is extremely low: on one hand, the root cause of the Cetus incident is a flaw in the Cetus math library, not an error in the protocol's pricing mechanism or underlying architecture. On the other hand, the vulnerability is limited to Cetus itself and is unrelated to the SUI code. The root of the vulnerability lies in a boundary condition check, and only two lines of code need to be modified to completely eliminate the risk; once the fix is completed, it can be immediately deployed to the mainnet, ensuring that subsequent contract logic is complete and eliminating this vulnerability.
High Concealment: The contract has been running smoothly for two years with zero faults, and the Cetus Protocol has undergone multiple audits, but no vulnerabilities were found. The main reason is that the Integer_Mate library used for mathematical calculations was not included in the audit scope.
Hackers exploit extreme values to precisely construct trading intervals, creating extremely rare scenarios with exceptionally high liquidity that trigger abnormal logic, indicating that such issues are difficult to detect through ordinary testing. These problems often reside in blind spots within people's sight, which is why they remain hidden for a long time before being discovered.
Move excels in resource safety and type checking compared to various smart contract languages, and it has built-in native detection for integer overflow issues in common scenarios. This overflow occurred because an incorrect value was used for the upper limit check when calculating the required token amount while adding liquidity, and bitwise operations were used instead of conventional multiplication. If conventional addition, subtraction, multiplication, and division were used in Move, it would automatically check for overflow situations, preventing such high-bit truncation issues.
Similar vulnerabilities have also appeared in other languages (such as Solidity and Rust), and they are even easier to exploit due to the lack of integer overflow protection; prior to the updates in Solidity, the checks for overflow were very weak. Historically, there have been issues such as addition overflow, subtraction overflow, and multiplication overflow, with the direct cause being that the result of the operation exceeded the range. For example, vulnerabilities in the BEC and SMT smart contracts of the Solidity language were exploited by carefully crafted parameters that bypassed the detection statements in the contracts, resulting in excessive transfers to achieve attacks.
3. The consensus mechanism of SUI
3.1 Introduction to SUI Consensus Mechanism
Overview:
SUI adopts a Delegated Proof of Stake framework (DeleGated Proof of Stake, abbreviated as DPoS)). Although the DPoS mechanism can improve transaction throughput, it cannot provide the extremely high level of decentralization like PoW (Proof of Work). Therefore, the decentralization level of SUI is relatively low, and the governance threshold is relatively high, making it difficult for ordinary users to directly influence network governance.
Average number of validators: 106
Average Epoch duration: 24 hours
Mechanism process:
Equity Delegation: Ordinary users do not need to run nodes themselves; they can participate in network security guarantees and reward distribution by staking SUI and delegating it to candidate validators. This mechanism lowers the participation threshold for ordinary users, allowing them to engage in network consensus by "hiring" trusted validators. This is also a significant advantage of DPoS compared to traditional PoS.
Representative round of block generation: A few selected validators produce blocks in a fixed or random order, which enhances confirmation speed and increases TPS.
Dynamic Election: After each voting period ends, a dynamic rotation is conducted based on voting weights to re-elect the Validator set, ensuring node vitality, interest consistency, and decentralization.
Advantages of DPoS:
High Efficiency: With a controllable number of block-producing nodes, the network can complete confirmations in milliseconds, meeting high TPS requirements.
Low cost: Fewer nodes participating in the consensus significantly reduce the network bandwidth and computing resources required for information synchronization and signature aggregation. As a result, hardware and operational costs decrease, the requirements for computing power decrease, and costs are lower. Ultimately, lower user transaction fees are achieved.
High security: The staking and delegation mechanism synchronizes the cost and risk of attacks; combined with the on-chain forfeiture mechanism, it effectively suppresses malicious behavior.
At the same time, the consensus mechanism of SUI adopts a BFT (Byzantine Fault Tolerance) based algorithm, which requires more than two-thirds of the votes among validators to reach consensus in order to confirm transactions. This mechanism ensures that even if a minority of nodes act maliciously, the network can remain secure and operate efficiently. Any upgrades or major decisions also require more than two-thirds of the votes to be implemented.
Essentially, DPoS is a compromise solution to the "impossible triangle," balancing decentralization and efficiency. In the security-decentralization-scalability "impossible triangle," DPoS chooses to reduce the number of active block producers in exchange for higher performance, sacrificing a certain degree of complete decentralization compared to pure PoS or PoW, but significantly improving network throughput and transaction speed.
3.2 The performance of SUI in this attack
3.2.1 The operation of the freezing mechanism
In this event,